
Cybersecurity
Has Never Been This Fun.
The Print & Play board game to learn about the OWASP Top 10 threat lists.
Defend your systems, exploit threats and become a legend
CONFIDENTIAL:
Situation Report
Subject: OWASP Top 10 "The Game".
Objective: You are a cybersecurity professional and your mission is to protect your organization's assets.
Use your knowledge of the 10 most critical vulnerabilities to deploy defenses, launch attacks and sabotage your opponents. Each game is unique, every decision counts. Do you have what it takes?
CONFIDENTIAL:
Situation Report
Subject: OWASP Top 10 "The Game".
Objective: You are a cybersecurity professional and your mission is to protect your organization's assets.
Use your knowledge of the 10 most critical vulnerabilities to deploy defenses, launch attacks and sabotage your opponents. Each game is unique, every decision counts. Do you have what it takes?

Characters

PENTESTER
PENTESTER
Penetration testing specialist. Evaluates the security of systems and applications by simulating real attacks to identify vulnerabilities.
Uses ethical hacking techniques, auditing tools and structured methodologies to discover security flaws before they are exploited by real attackers.
Components
Action Cards



These are the fundamental cards of the game that determine each player's actions in each round.
Protection Card
Represents a defensive action. When this card is played, the player is trying to protect a system threat against possible attacks.
Attack Card
Represents an offensive action. When this card is played, the player is trying to exploit a system vulnerability.
Action Cards
These are the fundamental cards of the game that determine each player's actions in each round.
Protection Card
Represents a defensive action. When this card is played, the player is trying to protect a system threat against possible attacks.
Attack Card
Represents an offensive action. When this card is played, the player is trying to exploit a system vulnerability.




Leader
The leader is the coordinator of the security team. Their role is fundamental to organizing defenses and coordinating the group's actions.
Responsibilities
Coordinates team actions, distributes action cards, and makes strategic decisions about which threats to prioritize.
Skills
Effective communication, strategic thinking and ability to motivate the team towards common security objectives.


Leader
The leader is the coordinator of the security team. Their role is fundamental to organizing defenses and coordinating the group's actions.
Responsibilities
Coordinates team actions, distributes action cards, and makes strategic decisions about which threats to prioritize.
Skills
Effective communication, strategic thinking and ability to motivate the team towards common security objectives.
Trust Indicator
The trust indicator is a visual indicator that shows the level of trust and collaboration between security team members. The blue tokens mark the team's current trust level.
High Level
Indicates that the team is working collaboratively and effectively, with good communication and coordination among all members.
Medium Level
Shows that there is some collaboration but communication and coordination levels can be improved.
Low Level
Indicates communication problems, lack of coordination or conflicts that can affect the effectiveness of the security team.






Trust Indicator
The trust indicator is a visual indicator that shows the level of trust and collaboration between security team members. The blue tokens mark the team's current trust level.
High Level
Indicates that the team is working collaboratively and effectively, with good communication and coordination among all members.
Medium Level
Shows that there is some collaboration but communication and coordination levels can be improved.
Low Level
Indicates communication problems, lack of coordination or conflicts that can affect the effectiveness of the security team.






The System Map
The system map is the visual representation of the infrastructure that the security team must protect. It shows the different areas and components that may be vulnerable to attacks.
Threat Areas
Each circle on the map represents a specific threat to the system that must be identified and protected by the team.
QR Codes
Each threat contains a QR code that provides detailed information about the vulnerability and how to mitigate it.
OWASP Green Tokens
When placed on the map, they represent OWASP Top 10 vulnerabilities that have been identified and successfully mitigated by the security team.
OWASP Red Tokens
When placed on the map, they represent OWASP Top 10 vulnerabilities that have already been exploited by attackers.
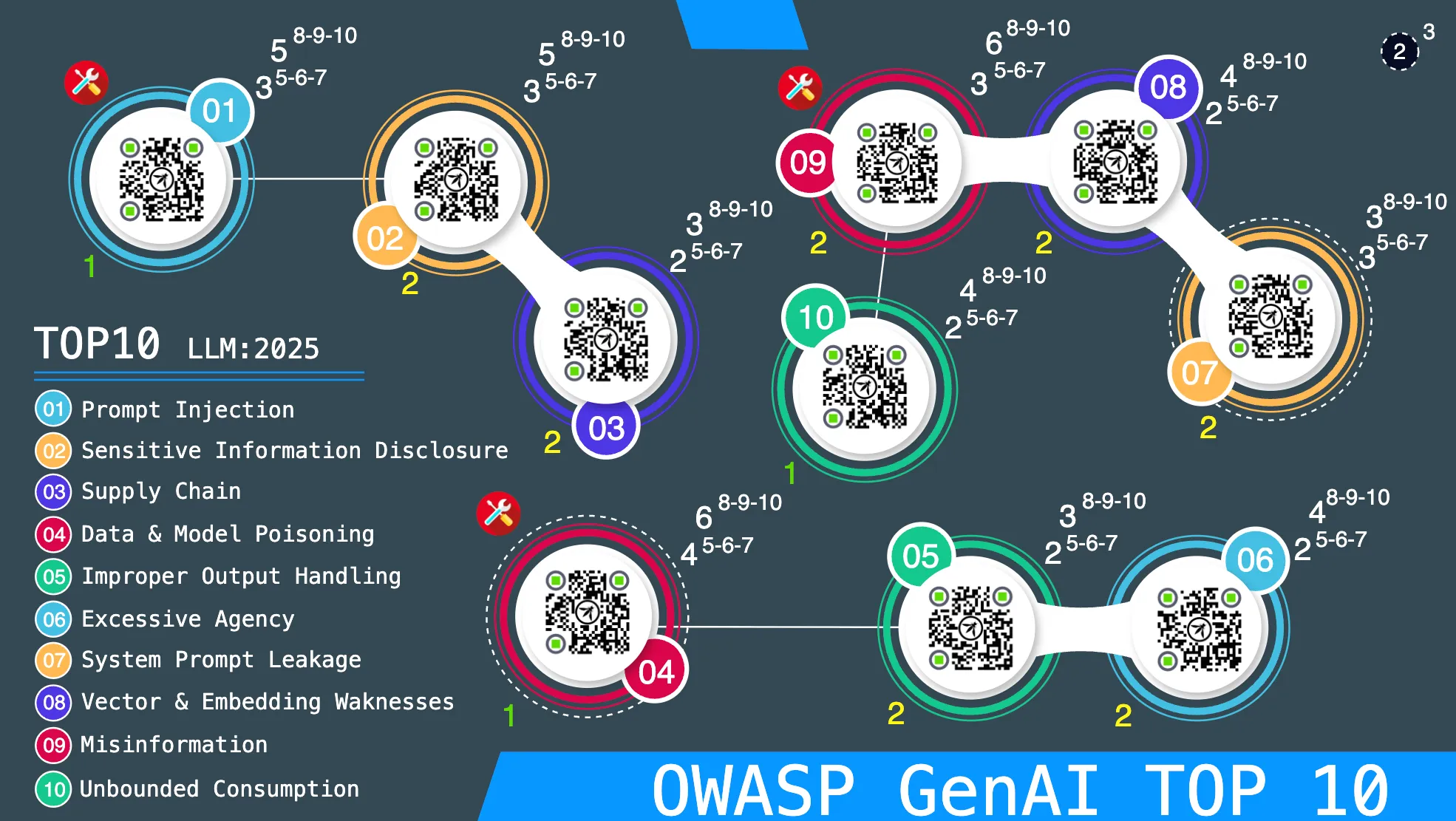










The System Map
The system map is the visual representation of the infrastructure that the security team must protect. It shows the different areas and components that may be vulnerable to attacks.
Threat Areas
Each circle on the map represents a specific threat to the system that must be identified and protected by the team.
QR Codes
Each threat contains a QR code that provides detailed information about the vulnerability and how to mitigate it.
OWASP Green Tokens
When placed on the map, they represent OWASP Top 10 vulnerabilities that have been identified and successfully mitigated by the security team.
OWASP Red Tokens
When placed on the map, they represent OWASP Top 10 vulnerabilities that have already been exploited by attackers.













Action Protocol
KICKOFF
Initial meeting where the system map is selected, employees are hired, and the first security team leader is chosen.
FOLLOW-UP MEETING
Allows restarting tasks, choosing a new leader, new team, and above all improving trust among everyone for new challenges.
RETROSPECTIVE MEETING
Final meeting where everyone faces each other and discusses openly what was done wrong and what was done right.
Complete Rulebook
System Map Selection Phase
In this phase, the system map card that the group of experts will study and protect must be selected. On this map, circles located in different areas will appear, which will be the threats that this system has.
- Inside they have a QR code and an identifier. If you capture that QR, you can read about that threat, learn about it, and also how it can be mitigated.
- Next to each threat on its right side appear a series of numbers. These numbers will have a base and an exponent.
- The base will be the number of team members that will be sent to defend that threat.
- The exponent will be a number or range of numbers, which must match the number of workers that have been hired by the company.
Hiring Phase
The following table shows the number of cards that should be used depending on the number of experts that the company will hire:
| Experts | The Good Guys | The Bad Guys |
|---|---|---|
| 5 | 3 | 2 |
| 6 | 4 | 2 |
| 7 | 4 | 3 |
| 8 | 5 | 3 |
| 9 | 6 | 3 |
| 10 | 6 | 4 |
Procedure:
- Keep the selected good guys cards separate from the selected bad guys cards.
- With the rest, create a deck of discarded cards.
- In the good guys card deck, you must add the CISO card if it wasn't there before.
- If the CISO card was already there, add one good guys card of your choice to the good guys deck.
- If the company has already hired all 10 experts, this task would not be necessary.
- Otherwise, you will now have one extra good guys card and you will have to shuffle that deck face down and discard one card without anyone seeing which one it is.
- Once the discard is done, join all the remaining good guys cards and the bad guys cards and shuffle them all.
- Deal one card to each person. These cards cannot be shown to anyone, only the card owner can look at it.
Secrets Phase
Standard procedure:
- You start with everyone with their eyes closed.
- The bad guys point to themselves with their index finger without opening their eyes and the CISO opens their eyes.
- The CISO must close their eyes again and the bad guys must stop pointing to themselves with their index finger.
- Finally all employees open their eyes.
Variant:
- Everyone closes their eyes and only the bad guys open their eyes. This way they know their companions.
- Now they close their eyes and the bad guys point to themselves with their index finger so the CISO opens their eyes and discovers who the bad guys are.
- The CISO must close their eyes again and the bad guys must stop pointing to themselves with their index finger.
- Finally all employees open their eyes.
Note: This procedure favors the bad guys because they know each other from the beginning.
Note: It may be the case that no one has the CISO card, but this procedure must continue to be followed because this will not be known until the game ends.
Kickoff Meeting
In this meeting, all hired employees meet each other and for the first time can talk to each other. They can say whatever they want, without any restrictions. They just cannot show their card to anyone.
System Study
They will have to study the map and understand well what this system offers.
Leader Election
They will have to agree to choose a leader. To do this, they will have to vote unanimously by pointing with their finger to the person that each one decides.
- The one with the most votes will be the new leader.
- In case of a tie, everyone will have to vote again for a leader among the employees who have tied with the most votes.
- Before voting again, you will have to remove from the trust indicator as many blue tokens as elected leaders minus 1.
- If you vote again and there is still a tie, blue tokens will continue to be removed following the same criteria.
- In the case that a blue token has to be removed from the trust indicator and there are none left, the bad guys will have won the game.
Threat and Team Selection
The leader will now be the one who decides which threat will be the first to protect and if anyone has any doubts about that threat, they will be responsible for explaining it.
Once selected, they must choose the team that will be responsible for protecting it. The number of members of that team will have to be the value of the base whose exponent is within the range or is the value of the employees that the company has hired.
To choose them, the leader must give each one an access credentials card and two action cards: the attack card and the protection card. In the case that the team has 6 members, the leader must choose 2 members from those 6 and give only one set of action cards.
Action Phase
It's time to protect the system from that latent threat. For this, the selected team members must secretly choose between one of the action cards. In the case of a 6-member team, the two employees who share a set of action cards will each take one and debate which one to choose in public, without showing the cards and without indicating which one each has.
The Good Guys
Who belong to the team, that is, who have the access credentials card, as expected, will choose the protection action card, although nothing prevents them from choosing the attack card if they understand it as strategy.
The Bad Guys
Those who have been given the access credentials card must also choose one of those action cards, but these are interested in the threat being exploited.
All members of that team hand over their chosen action card to the leader and he will shuffle them without anyone, including the leader himself, seeing which card each member has delivered.
Results Report Phase
The leader gathers all employees and begins to reveal the action cards one by one, but they can decide, if the threat has already been exploited, not to continue revealing cards. If this action is taken, a blue token must be removed from the trust indicator. If there are no tokens left to remove, the bad guys will have won the game.
Threat Exploited
If at least one of the action cards shown is an attack card, the threat has been exploited and a red OWASP token is placed on the circle of that threat.
Threat Contained
On the contrary, if all the revealed action cards are protection cards, the threat has been contained and mitigated and a green OWASP token must be placed.
Important notes:
- In some threats, exploiting them will be much more complicated than normal, requiring at least two attack action cards. These threats are marked with a double circle with a dashed line.
Protection Layers
In some maps there are protection layers or levels and threats are distributed within these levels. These layers are differentiated by the level number that will appear on the left side of each of the threat circles.
- A level 1 layer will be the most exposed layer of the system.
- A level 3 layer will be the most internal layer of the system.
- If the good guys manage to protect each and every threat in a layer, then the inner layers on which nothing has been done yet will become protected.
- If, on the contrary, a threat in a layer is already exploited, that layer can no longer be fully protected.
Retrospective Meeting
This meeting is activated when:
Good Guys Victory
If the number of protected threats is greater than the sum of unprotected threats plus those remaining to be decided, the good guys have successfully protected the system entirely.
Bad Guys Victory
If the number of exploited threats is greater than or equal to the number of protected threats plus those remaining to do something, then the bad guys have hacked the system.
Last Chance for the Bad Guys
In the case that the system has been protected, the bad guys have one last chance: to say who among all the employees is the CISO.
- For this, all employees will have to vote unanimously by pointing with their finger if the standard procedure was performed in the secrets phase, or only the bad guys if the variant was used.
- In any case, only the votes of the bad guys will count, although all employees' cards will be revealed in clockwise order starting from the last chosen leader.
- If all the bad guys point to the CISO, they are the winners.
- If one or more of the bad guys fail, they will have lost definitively.
- If each of the bad guys points to themselves and there is no CISO hired as an employee, the bad guys will have won the game.
Important: Cards should not be revealed yet until after this phase.
Follow-up Meeting
In the case that the criteria to activate the retrospective meeting are not met, follow-up meetings are activated.
Procedure:
- These meetings restart the round.
- They cause a blue token to be added to the trust indicator if the threat in the previous round was contained or a blue token to be removed from the trust indicator if it was exploited. If a blue token must be removed from the trust indicator and there are none left, the bad guys will have won the game.
- The access credentials cards are returned to the leader and the action cards are also returned to him without anyone seeing them.
- The leader must shuffle them when receiving them along with the ones he already had.
- It's time to choose a new leader again and start the process over.
Extension - Team Building
In this game mode, Team Building cards will be distributed as described below in the kickoff meeting or in follow-up meetings by the new leader immediately after being elected.
Deck Preparation
First, the team building card deck must be prepared at the beginning of the kickoff meeting depending on the number of employees hired.
For this, you must observe the numbers that appear next to the circle on its right side on each of the team building cards. Select to create the deck the cards that have in their exponent the number or range of numbers of employees that the company has hired.
Card Distribution
Once this deck is created and the leader is chosen, they will draw from this previously shuffled deck:
- 3 cards for companies that have hired 8-9-10 employees
- 2 cards for 5-6-7 hired employees
Only they will be able to see them. Then they will hand these cards to another employee who will shuffle them and deliver them in the order indicated by the leader to the employees they choose, but neither they nor their assistant will be able to see which card is delivered to each employee.
Card Usage
Once the team members are chosen, those who have a team building card and are part of the team, one by one, must show it to everyone following the clockwise order from the position where the leader is located.
Each member must apply their effect if it is of "immediately" type or decide whether they want to apply their effect in this round if it is of "1 use only" type. If they decide not to apply their effect, they must leave the card visible.
It is possible that team building cards were previously assigned from previous rounds, if any of them belong to one of the team members, they can apply their effect if they so decide.
Team Building Cards List
Confidence (Immediately)


If the leader assigns you this card, you will have to ask them to show their employee card to any employee you decide, including yourself. (In the case that the bad guys were known in the secrets phase, it is the leader who chooses who to show it to)
Effect: This card forces you to add a blue token to the trust indicator.
Return your card to the discard deck.


If the leader assigns you this card, you will have to ask them to show their employee card to any employee you decide, including yourself. (In the case that the bad guys were known in the secrets phase, it is the leader who chooses who to show it to)
Effect: This card forces you to add a blue token to the trust indicator.
Return your card to the discard deck.
Take Control (Immediately)


If the leader assigns you this card, you will become the new leader and you have to choose threat and team again. This new leader blocks the process and use of team building cards in this round. If someone has an "immediately" card, they will have to discard it immediately.
Effect: This card forces you to remove a blue token from the trust indicator.
Return your card to the discard deck.


If the leader assigns you this card, you will become the new leader and you have to choose threat and team again. This new leader blocks the process and use of team building cards in this round. If someone has an "immediately" card, they will have to discard it immediately.
Effect: This card forces you to remove a blue token from the trust indicator.
Return your card to the discard deck.
Rejection (1 use only)


If the leader assigns you this card and you are selected for a team, you must reject the leader's choice and decide it yourself directly, restarting the threat and team selection and team building card distribution process. If someone has an "immediately" card, they will have to discard it immediately.
Effect: Using this card forces you to remove a blue token from the trust indicator.
When using it, return your card to the discard deck.


If the leader assigns you this card and you are selected for a team, you must reject the leader's choice and decide it yourself directly, restarting the threat and team selection and team building card distribution process. If someone has an "immediately" card, they will have to discard it immediately.
Effect: Using this card forces you to remove a blue token from the trust indicator.
When using it, return your card to the discard deck.
Peer Review (1 use only)


If you have this card and you are selected for a team, you can choose another person who is not on the team to be part of it and be given an access credentials card, being a full member even if the number of team members indicated in the threat is exceeded (Except for teams that are already 6 members, which will have no effect).
When used, return your card to the discard deck.


If you have this card and you are selected for a team, you can choose another person who is not on the team to be part of it and be given an access credentials card, being a full member even if the number of team members indicated in the threat is exceeded (Except for teams that are already 6 members, which will have no effect).
When used, return your card to the discard deck.
To Accept Responsibility (1 use only)


If the leader assigns you this card and you are selected for a team, you must choose to change one person on the team for another that you decide who has not been selected.
When used, return your card to the discard deck.


If the leader assigns you this card and you are selected for a team, you must choose to change one person on the team for another that you decide who has not been selected.
When used, return your card to the discard deck.
Random Seed (1 use only)


If the leader assigns you this card and you are selected for a team, you must choose a team member, or even yourself, and be the one who blindly chooses their action card.
When used, return your card to the discard deck.


If the leader assigns you this card and you are selected for a team, you must choose a team member, or even yourself, and be the one who blindly chooses their action card.
When used, return your card to the discard deck.
Shadower (1 use only)


If the leader assigns you this card and you are selected for a team, you must choose a member and only you will see the action card chosen by that member. You must say out loud the name of the employee you are going to observe so that when the action phase arrives, they show you that card.
When used, return your card to the discard deck.


If the leader assigns you this card and you are selected for a team, you must choose a member and only you will see the action card chosen by that member. You must say out loud the name of the employee you are going to observe so that when the action phase arrives, they show you that card.
When used, return your card to the discard deck.
Busted (1 use only)


If the leader assigns you this card and you are selected for a team, you can, if you so wish, change the status of an already protected threat to attacked. To do this, you must flip that threat's token from green to red.
Effect: Using this card forces you to remove a blue token from the trust indicator.
When used, return your card to the discard deck.


If the leader assigns you this card and you are selected for a team, you can, if you so wish, change the status of an already protected threat to attacked. To do this, you must flip that threat's token from green to red.
Effect: Using this card forces you to remove a blue token from the trust indicator.
When used, return your card to the discard deck.
Perseverance (1 use only)


If the leader assigns you this card and you are selected for a team, you can, if you so wish, change the status of an already attacked threat to protected. To do this, you must flip that threat's token from red to green.
Effect: Using this card forces you to add a blue token to the trust indicator.
When used, return your card to the discard deck.


If the leader assigns you this card and you are selected for a team, you can, if you so wish, change the status of an already attacked threat to protected. To do this, you must flip that threat's token from red to green.
Effect: Using this card forces you to add a blue token to the trust indicator.
When used, return your card to the discard deck.
Security Tool (Entire game)


If the leader assigns you this card and you are selected for a team, you can eliminate an attack card in the results report phase if you so decide.
There may be maps where this tool directly protects threats that have a tool symbol in the upper left part of the circle. It will not be necessary to do the action phase if you decide to use the effect of this card, you can directly place a green token on the threat.


If the leader assigns you this card and you are selected for a team, you can eliminate an attack card in the results report phase if you so decide.
There may be maps where this tool directly protects threats that have a tool symbol in the upper left part of the circle. It will not be necessary to do the action phase if you decide to use the effect of this card, you can directly place a green token on the threat.